Client
A high-traffic digital platform experiencing frequent traffic spikes caused by mobile clients, web requests, and occasional bot or malicious behavior.
The backend system suffered from:
-
Request floods
-
Abusive traffic patterns
-
API misuse
-
Sudden spikes during peak campaigns
They needed a layered protection system combining rate limiting, traffic throttling, and intrusion mitigation.
Project Overview
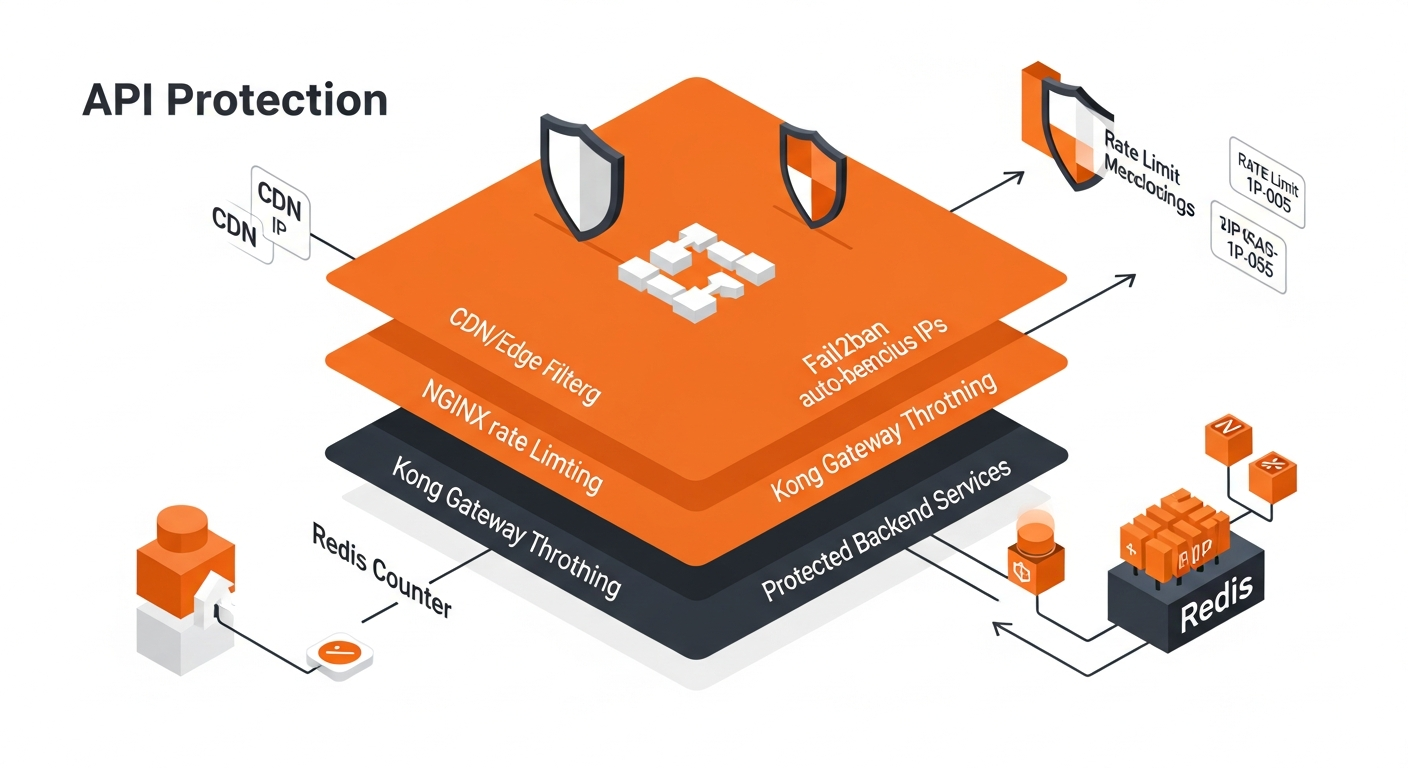
We implemented a multi-layer protection architecture using:
-
NGINX rate-limiting modules
-
Kong Gateway throttling plugins
-
Fail2ban for bot and abusive IP blocking
-
Custom token-bucket and sliding-window logic
-
Redis-backed counters for distributed rate limits
-
Monitoring dashboards for real-time visibility
The objective was to stabilize the API platform under heavy load while protecting backend services from abusive clients.
Key Challenges
1. Sudden Traffic Spikes
Unexpected bursts were overwhelming application servers and database connections.
2. Lack of Abuse Detection
The existing system could not identify suspicious IPs or malicious retry loops.
3. No Unified Edge Protection
Traffic handling happened directly at application level, leading to overload.
4. Multi-Client Ecosystem
Public users, partner APIs, internal services, and automated systems all required different throttling rules.
Our Solution
1. NGINX Rate Limiting
We implemented NGINX as the rate-control layer using:
-
limit_req_zoneandlimit_req -
Per-IP throttling
-
Separate limits for public and private APIs
-
Burst control to absorb short spikes
This reduced immediate pressure on backend services.
2. Kong API Gateway Throttling Policies
For advanced control, we configured Kong with:
-
Consumer-level rate limits
-
Key-based quotas
-
Sliding-window counters
-
Redis-backed distributed caching
-
Route-specific throttle rules
This supported dynamic adjustments without redeploying services.
3. Fail2ban for Abuse Detection and Automatic Banning
To stop malicious actors and bot attacks, we integrated Fail2ban into the traffic protection stack.
Fail2ban monitored:
-
NGINX logs
-
Kong Gateway logs
-
Authentication failures
-
Suspicious request patterns
-
Excessive 4xx/5xx responses
-
Repeated rate-limit violations
Actions implemented:
-
Automatic temporary IP bans
-
Permanent bans for repeat offenders
-
Email notifications for security staff
-
Log aggregation for analysis
Fail2ban served as the security firewall that blocked abusive traffic before it reached application services.
4. Custom Throttling Logic
Some scenarios required more precise control than standard tools.
We built custom logic using:
-
Token bucket algorithm
-
Sliding window algorithm
-
Client-type–based throttling (mobile vs. partner API vs. internal)
-
Device-level request control
-
Circuit breakers for overload protection
This allowed fine-grained throttling on critical endpoints.
5. Monitoring, Metrics & Observability
We added:
-
Prometheus metrics for throttle and ban events
-
Grafana dashboards for traffic patterns
-
Alerting on spike anomalies
-
Logs for banned IPs and throttled requests
Teams gained complete visibility into API health and abuse attempts.
Architecture Diagram (Text Version)
Results & Impact
Stable Performance
API performance remained stable even during heavy spikes.
Backend Protection
Fail2ban significantly reduced malicious traffic before it reached the API gateway.
Lower Error Rates
Throttling and banning reduced overload-related failures.
Predictable System Load
CPU, memory, and DB load stayed within controlled thresholds.
Faster Incident Response
Centralized logs made it easy to identify abusive clients.
Scalable Protection
Rules can be tuned per IP, token, route, or client category.
Conclusion
By implementing a combination of NGINX rate limiting, Kong Gateway throttling, Fail2ban intrusion detection, and custom throttling algorithms, we delivered a layered protection system that stabilizes API performance under high traffic and blocks malicious behavior.
The final architecture ensures:
-
Controlled request flow
-
Automatic detection and banning of abusive clients
-
Reliable backend performance
-
Protection from floods, bots, and misconfigured clients
The system is now resilient and ready to scale securely.

Written by
Oliver Thomas
Oliver Thomas is a passionate developer and tech writer. He crafts innovative solutions and shares insightful tech content with clarity and enthusiasm.